Vulnerability Management
Overview
O7Lab Vulnerability Management services deliver proactive scanning, testing and remediation of application, database, servers and network vulnerabilities so you can combat against the threats and better protect your customer data, intellectual property, financial information and other key assets
Our vulnerability management program is performed via automated and manual testing methodologies to reduce the incidence of false positives. Our experts are here to help you quickly leverage your security program investment by handling the operational requirements of vulnerability scanning.
Our Process
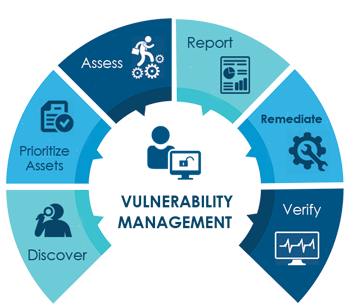
Discover
It is the information gathering phase where we collect the inventories. It is otherwise called as preparatory phase in vulnerability management process. Discovery phase will find every server, applications and network connected components.
Verify
After the application of patches and remediation process, organization should do re-assessment of network connected assets to ensure that fix works properly and it does not cause other network devices, services or applications to malfunction.
Prioritize Assets
Once the list of assets is confirmed, next step is to prioritize them based on their importance. It is Pre-Assessment Phase. Prioritizing assets according to their criticality is the key determining where to take the action first.
Report
Once assessment is completed, all the verified vulnerabilities will be provided with proof of concept and remediation plans as a comprehensive report. Reports can be used for tactical operational tasks, to provide visibility and business oriented risk metrics to management.
Assets
It includes network (internal and external) scanning, firewall logging, configuration scan, penetration testing and using the automated vulnerability scanners. Identify and verify known vulnerabilities on the servers, applications and systems. All the identified and verified vulnerabilities needed to be classified based on severity and the level of risk it presents to organization.
Remediate
It includes technical measures such as the patch fixing, configuration of firewalls or other network & host based vulnerability. Remediate high-risk vulnerabilities based on risk level, risk of compromise and impact of compromise. During this process, our expert team will assist you in fixing the issues.
Benefits
- Fix vulnerability in software affecting the security, performance and functionality
- Identify the possible entry points or weak nodes in the network
- Automated and manual testing ensures that entire web application is assessed and vulnerabilities identified
- Increased scan efficiency based on current threat landscape
- Discover and categorize assets according to their criticality to your business
- Find the internal and external attack vectors
- Mitigate the known vulnerabilities
Deliverables
- Daily Asset Discovery
- Technical Severity Report
- Asset Classification and Grouping
- Customisable reports based on client requirement
- Remediation Tracking & Verification
- Compliance Reports
Are you ready to strengthen your network? Let's Talk / Connect with us for your security needs
1234567890
